Now offering in-person and virtual training!
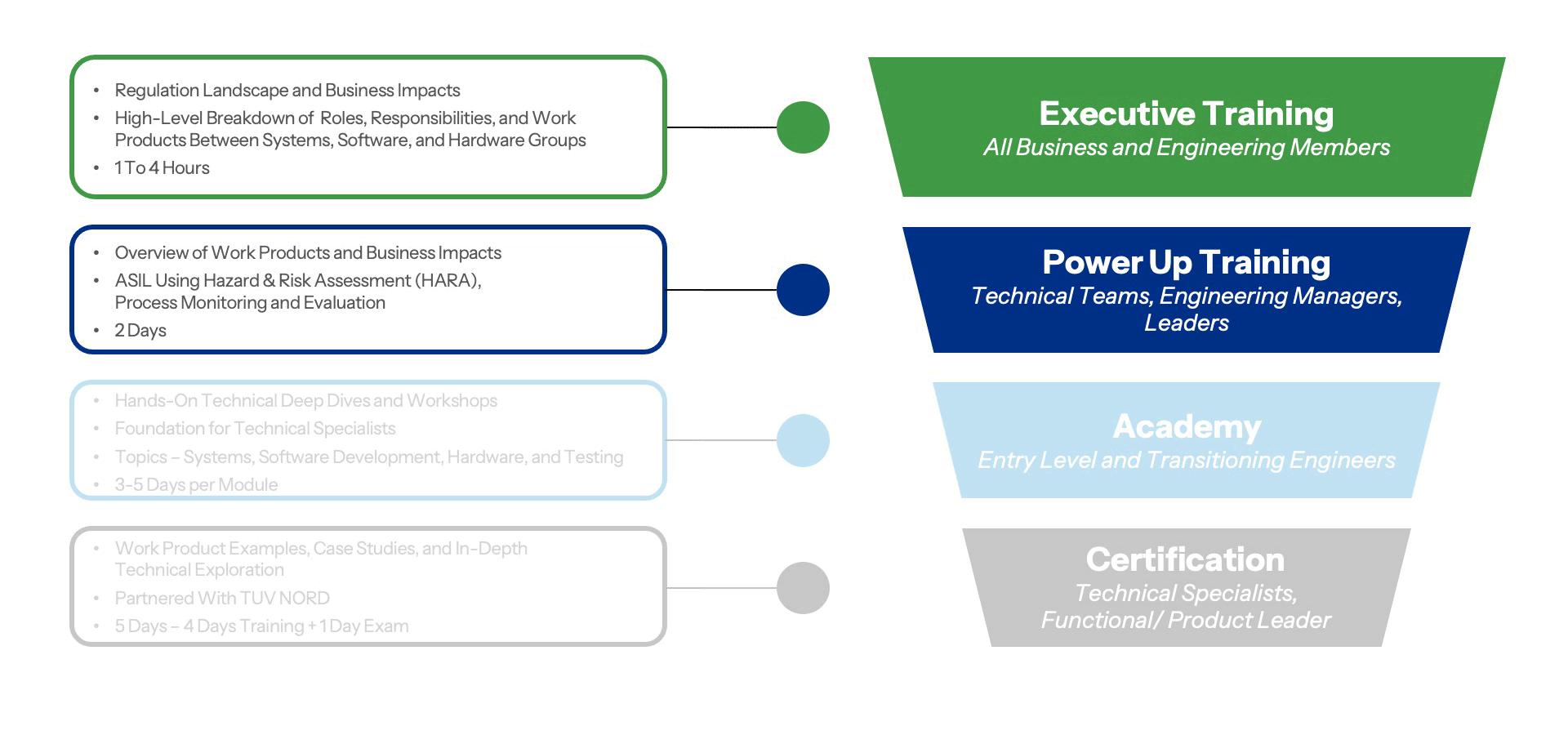
Power Up: Executive-level
Embedded Cybersecurity Training
Under the guidance of senior-level embedded Cybersecurity-experienced instructors, you will be exposed to a better understanding of the implementation of cybersecurity, and its management, analysis, monitoring, and evaluation processes.
Sign Up Now
Power Up Overview: Executive-level
Embedded Cybersecurity Training
From conception to production, functionally safe vehicles must be protected against the criminal or unauthorized use of, or attacks against, the electronic data and systems that are the lifeblood of these modern mechatronic machines. New and existing products must follow the proper measures to avoid, detect, and control these threats. Organizations must understand how to recognize these threats and mitigate them effectively.
Our Cybersecurity Power-Up Training will describe the meaning of cybersecurity and what is being done in the automotive industry to integrate these critical processes and safeguards. You will gain insight into each cybersecurity consideration, and the impacts they have on your organization and your customers.
What are the learning objectives?
- Standards: Learn how to articulate the purpose of ISO/SAE 21434. Compare and contrast the impacts of relevant standards from:
- NIST: National Institute of Standards and Technology
- ISO: International Organization for Standardization
- DIN: German Institute for Standardization
- ANSI: American National Standards Institute
- IEC International Electrotechnical Commission
- Cyber Management:
- Learn how to articulate overall cybersecurity management, including governance, culture, management and information systems, tool management, and audits.
- Understand the activities related to project-dependent cybersecurity management.
- Threat Analysis and Prevention:
- Work through a Threat Assessment and Remediation Analysis (TARA) case study.
- Work through a Threat Assessment and Remediation Analysis (TARA) case study.
- Process Monitoring and Evaluation:
- Understand the processes for monitoring, evaluation, vulnerability analysis, and management.
- Explain the distribution of cybersecurity activities and how to work with the supplier.
Course Overview
-
Day 1
-
Clause 1: Scope
-
Clause 2: Normative References
-
Clause 3: Terms and Definitions
-
Clause 4: General Considerations
-
Clause 5: Organizational Cybersecurity Management
-
Clause 6: Project Dependent Cybersecurity Management
-
Clause 7: Distributed Cybersecurity Activities
-
Clause 8: Continual Cybersecurity Activities
-
-
Day 2
-
Clause 9: Concept
-
Clause 10: Product Development
-
Clause 11: Cybersecurity Validation
-
Clause 12: Production
-
Clause 13: Operation and Maintenance
-
Clause 14: End of Cybersecurity Support and Decommissioning
-
Clause 15: Threat Analysis and Risk Assessment Methods
-
On-site Sessions
Customer's Location
Call for Quote 812-373-0880
For Groups of up to 20 Engineers
Meet your Presenters
Kelly Stephenson
Solutions Architect, Cyber Security
Kelly is a Solutions Architect in Cyber Security with over 30 years of engineering experience in automotive and industrial IoT products. Kelly is an innovative security engineer with extensive cybersecurity and software development experience within automotive design markets.
David Ha
Senior Embedded Cyber Security Engineer
David Ha joined LHP in 2021 as a Senior Embedded Cybersecurity Engineer with over 20 years of experience in cybersecurity product development, systems integration, verification, debugging, and failure analysis. He is also proficient in project management in all phases of development, from system design to requirements definition for the security of embedded devices (SoC, IoT, automotive, smart card), and system headend/backend
Our Training Funnel