Trustworthiness and the Autonomous Vehicle with the LHP Ecosystem
Self-driving vehicles are coming. There’s a certain sense of inevitability. Mentions appear almost daily in the news with players such as Tesla,...
Unlock Engineering Insights: Explore Our Technical Articles Now!
Discover a Wealth of Knowledge – Browse Our eBooks, Whitepapers, and More!
Stay Informed and Inspired – View Our Webinars and Videos Today!
Exploring the future of software-defined vehicles through expert insights.
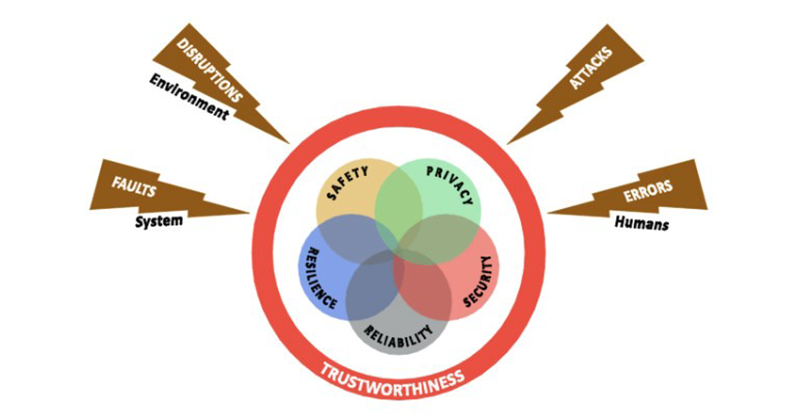
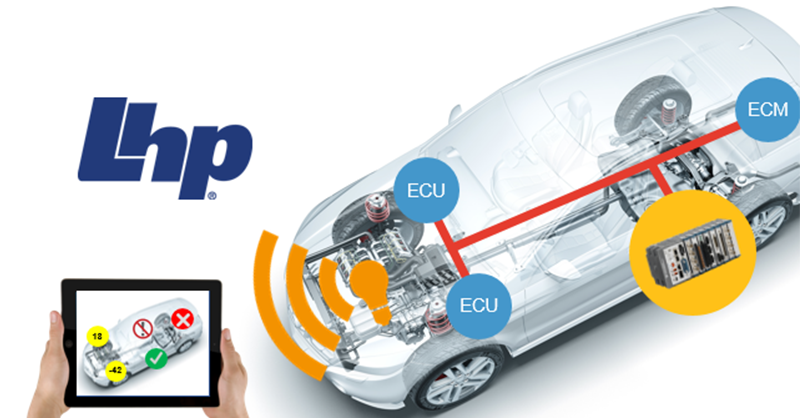
When contending with the complicated and interconnected devices of the Industrial Internet of Things (IIoT), the question of trustworthiness is often introduced. How do we make certain that the systems as designed are worthy of trust? Questions like this are intuitive and necessary, of course. However, they often lack the rigorous framework needed for a robust implementation in system design. “Trust” is a word that we may all think we understand, but when applying it to a network connected device in a crucial automotive subsystem, the word’s precise formulation becomes paramount.
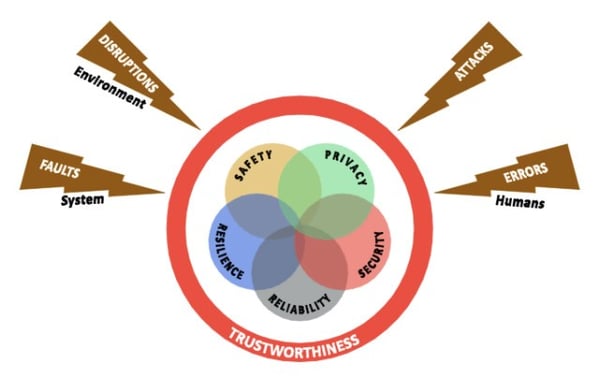
Introduction of trustworthiness from the Industrial Internet Consortium
Considering this, the Industrial Internet Consortium (IIC) has refined the definition a great deal, formulating it around five Key System Characteristics (KSCs): safety, security, stability, resilience, and privacy. Formally, the IIC defines trustworthiness as the “degree of confidence one has that the system performs as expected” within the boundaries set by the KSCs.
In “A Short Introduction into Trustworthiness,” a white paper for the IIC, Sven Schrecker, Vice President and Chief Architect, Cyber Security for LHP, alongside Marcellus Buchheit, President and CEO of Wibu-Systems USA, and Frederick Hirsch, Standards Manager at Fujitsu, offer a summary of each of the five KSCs that can help provide a clearer formulation of how to implement trustworthiness in operational technology (OT), using a vehicle as an example.
Safety is quite simply the trait that “ensures that a system operates without unacceptable risk,” of physical injury to human operators and users, while also avoiding property damage or negative impacts on the environment. Within the automotive field, the functional safety standard, ISO 26262, is in place to ensure safety for the operating systems of the vehicle. However, without a broader sense of how safety impacts each level of technological development within each interlocking system, complete safety is not guaranteed. Since there is no requirement for assessing cyber security as part of the automotive functional safety validation process, the integrity of the safety systems themselves can be called into question even on a previously certified vehicle.

Security refers to the design of a system in such a way that protects it from “unintended or unauthorized access, change or destruction.” Security covers not only the “traditional” needs of the installation of fences and locks, but also the “availability, integrity, and confidentiality of data at rest, in motion, or in use.” Due to the connected nature of vehicles on the road today, the security is crucial to the safety of the operator. Vehichle to vehicle (V2V) and vehicle to infrastructure V2x communication are integral to an autonomous vehicle’s design. However, these communication networks are often open and available for disruption from an outside force. Security on the vehicle prevents those outside forces from introducing anything malicious into the system. In this way, security is simply analogous to a lock, fence, or security system that protects our homes from unauthorized access.
The characteristic of reliability provides a framework for the ability of a system to operate as desired under normal conditions for an explicitly defined period. Reliability must provide for physical wear-and-tear on a system, in addition to such considerations as changing software versions over time. In the automotive field, this is self-evidently important. Vehicles on the road are subject to a tremendous range of potential hazards both from the environment and from users under normal operating circumstances. Traveling thousands of miles through a range of punishing climates, for example, is comfortably within the realm of normal operation for most vehicles, and as such they must be designed to be reliable under those conditions.
Resilience might usefully be framed as reliability “in the face of disruption.” As opposed to reliability, however, resilience “addresses unexpected and unplanned system statuses” that can result from a variety of errors injected into the system. Without resiliency, any disruption or unauthorized access to a vehicle system could cause irreparable damage to the components or operator. Resilience holds the system together; for instance, a back-up generator kicks-on when power is shut off to eliminate loss of operation.
Finally, privacy is designed to allow individuals interacting with the system to “control or influence what information related to them may be collected and stored,” and further how that information is then shared down the line. In a digital age where personal information is stored, shared, and distributed on a regular basis, consumers need to feel in control of what they do and do not allow. This also holds true in vehicles as they become more connected. The millions of sensors tracking and reporting data from the vehicle introduce privacy concerns that are new to automotive, to be sure. However, privacy is the backbone of trustworthiness in the eyes of a consumer as it allows the consumer to manage the data, systems, and information collected, sent, and stored.
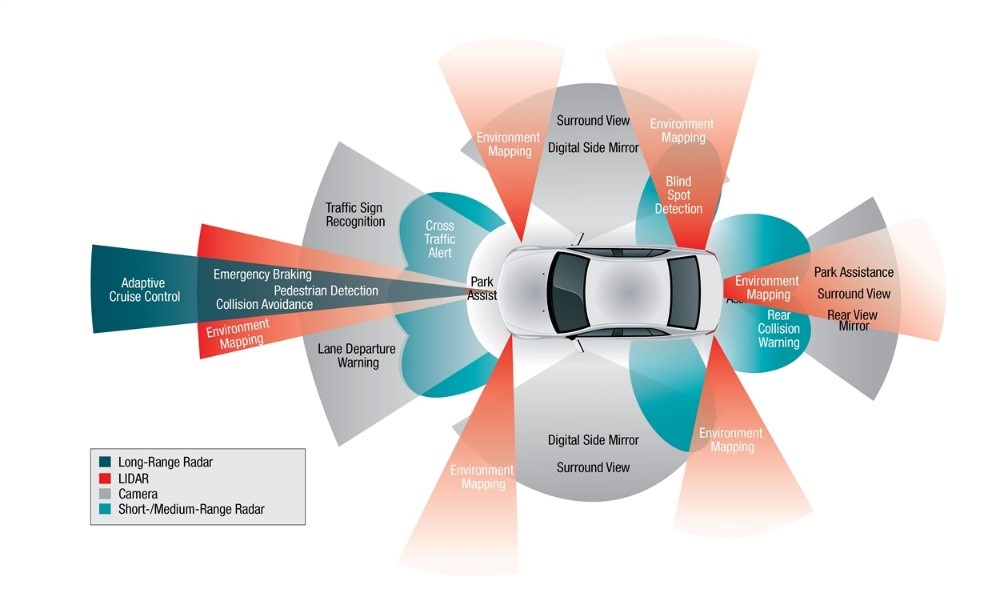
Car sensor of an autonomous or connected vehicle- Source: SAE (https://www.sae.org/dlymagazineimages/15067_24935_ACT.jpg)
It is important to note that none of these KSCs exist in a vacuum. In most cases, their importance will ebb and flow depending on the context. Further, it stands to reason that they are often interdependent, and in fact in some cases may be directly opposed to one another. For example, security as a KSC exists specifically to protect the system from the “malicious” or “erroneous” impacts of humans and the environment on the system, while on the other hand, the safety KSC “protects humans and the environment from any bad behavior of the system.”

In light of this complexity, it is clear that the implementation of these KSCs requires a responsive and integrated approach at levels of the design process. Schrecker, Buccheit, and Hirsch describe this approach as “trustworthiness by design,” and propose a framework called the “permeation of trust” to help guide the process. In this framework, the five KSCs are closely considered at every level of design, from operational users to system builders, all the way down to component builders.
Obviously embedding trustworthiness into every step of the design process will not happen overnight, and it will not be simple. But with the increasing reliance on connected devices throughout the industrial and automotive process, it is indispensable.
For more information on cyber security and the safety within the vehicle, contact LHP today.
Self-driving vehicles are coming. There’s a certain sense of inevitability. Mentions appear almost daily in the news with players such as Tesla,...
Powered by: LHP Engineering Solutions, AASA Incorporated, National Instruments, and PTC LHP Engineering Solutions, an engineering services provider...