Automotive Functional Safety and Cybersecurity Platform
LHP will be at the 2018 IoT Solutions World Congress Showcasing Embedded Cybersecurity On a Vehicle Platform
Unlock Engineering Insights: Explore Our Technical Articles Now!
Discover a Wealth of Knowledge – Browse Our eBooks, Whitepapers, and More!
Stay Informed and Inspired – View Our Webinars and Videos Today!
Exploring the future of software-defined vehicles through expert insights.
11 min read
![]() Kelly Stephenson
:
May 3, 2023 3:18:33 PM
Kelly Stephenson
:
May 3, 2023 3:18:33 PM

Table of Contents
When organizations start down the path of integrating cybersecurity into their processes and culture, this is a direct and very important question for them to ask. And the short and cryptic answer is, “it depends”.
The right level of attention for automotive cybersecurity will naturally vary from one organization to the next, because no two organizations are the same. This fundamental truth leads to additional questions:
Having the right amount of cybersecurity is an important but sometimes challenging balancing act. If a person becomes a cybersecurity zealot and over-subscribes, over-implements, and spends too much time and money implementing cybersecurity, then the cost of the product will be driven up, it will become more expensive than the market wants to bear, and the organization will become less competitive.
Many knock-off products have no cybersecurity in them. This makes them much cheaper to produce, and those manufacturers do not pay any cybersecurity teams to make them safe.
In contrast, the companies whose products they are knocking off have well-earned reputations for being cyber-secure. They have invested in the functional safety teams and cybersecurity teams and have put in place the tools and resources to properly perform this important work. Their products are secure, and they have a well-earned reputation for trustworthiness.
However, consumers tend to focus on getting the most features for the lowest cost. If they have a vague notion that a certain brand’s products are trustworthy, they tend to project that trustworthiness to the brand’s entire family of products, earned or not. And if the knock-off competitors look similar or seem similar, consumers tend to extend that notion of trustworthiness to the knock-off competitors as well.
It is competitive. The playing field is not level. And it certainly is not fair. At the end of the day, people are thinking about features and they're not thinking about other considerations like safety, which might be much more important. If the organizations producing the knockoffs take shortcuts, and they're not putting that kind of development money into securing their product or making it safe, then they have an upper hand financially.
This issue is compounded by the reality that few customers ask for cybersecurity. It is not a feature; it is just expected, preventative. It only matters when something bad happens. And that is the moment that everything can change.
A customer may own a product for its entire designed lifetime. And during that lifetime, nothing bad happens. No accidents, no hacking events, no system failures. For a company that has invested nothing into cybersecurity, it might seem like they have won. But the moment something negative happens, that all changes in a heartbeat. People start thinking, “Oh, this product is a piece of garbage.” They don't trust that company anymore, and the organization’s reputation is lost.
If the slighted business is a shadow company that exists to flood the market with knockoff junk that has not been tested or made safe, they probably won’t care. These types of companies are disposable. An unscrupulous person selling junk while hiding behind three shell companies will likely be long gone with the money in hand by the time bad things start to happen. And in many markets, they can get by with it because consumer products are constantly changing at a rapid pace; most consumers have very short attention spans and are easily distracted by the next shiny thing.
But the automotive realm is different. Automotive brands have longevity. Their reputations can easily span multiple generations. Vehicles that stand out because of their ruggedness, reliability, design, performance, safety, or overall value, become legendary and cast a favorable glow on their maker that lasts long after they have gone out of production. And models that fall short of the mark become notorious, the butt of jokes, and forever a stain on the company that made them.
Yes, it is tough to compete if you are doing things the right way. But most automotive OEMs are doing things the right way or trying to move in the right direction with cybersecurity because they are experienced enough to see the big picture and understand both the nature of the business and the ramifications.
Some organizations will go ahead and do the right thing. They're doing their due diligence and making sure cybersecurity and functional safety are taken care of. But there have also been all kinds of cases where cybersecurity breaches have taken place and sensitive information has been lost, and customers have been put at risk. You certainly don't want to be a company that has that problem.
When a cybersecurity lapse plays out in the news, it tends to follow a familiar pattern: A news story breaks on how the latest cybersecurity attack has brought harm to the customers of a certain company, and then they replay “breaking news” updates of variations on that story for two weeks straight, airing them many times a day, sometimes, many times an hour. And if they can add spectacular visuals that graphically underscore the effects of the failure? And it is a slow news day? … No company wants that kind of damage inflicted upon their reputation.
With social media and all of the news outlets available today, communication is instant, and the news cycle is constant. If an organization suffers some sort of a cybersecurity breach, everyone is going to know about it, and quickly.
If that organization builds cars, all of their existing customers are going to start wondering if their cars are safe as well, even if they don’t own the same model or model year. The recent swarm of airbag recalls has educated the public on the notion that a given defective part might be used in multiple makes, models, and model years. It can be too much to easily parse, so they target their concern on the handle that is easiest to grasp: the brand, the logo. Is this brand of car secure? Do I want to buy a car from this company if they have a reputation for losing sensitive customer information or placing customers at risk with flawed or vulnerable digital systems or other safety issues? Does choosing this particular brand of car put my life at greater risk? If the customer concludes that the answer is “yes”, there is a good chance that they will dispose of that vehicle quickly and never buy another car from that company ever again.
And they will tell their friends and family all about it. Often.

Some attacks that can impact car systems are purely physical, crude and brute force in nature, such as breaking into the vehicle and activating the starting system through the steering column by popping the key slot really hard with a screwdriver and starting the car with it. Once the vehicle is turned on, all systems can be accessed as if the bad actor legitimately had the keys. A damaged ignition switch is a cheap price to pay in exchange for gaining possession of an entire vehicle that can then either be repaired or disassembled and sold for parts.
But the types of modern attacks that are seeing the most growth in number and complexity are almost all digital in nature. And in many instances, bad actors are no longer attacking the car directly in order to steal it, they are instead attacking the devices that the legitimate owners use to access those cars.
For example, there are vehicles where the driver’s phone can be used as a key. The car company makes the software, but they don’t provide the phones. And due to the staggering variety of phone types, operating systems, software versions, and configurations, car companies are limited in what they can control and safeguard against on the phone side. These systems can be vulnerable because the phone can be a weak point due in large part to this complex array of possible phone configurations.
Likewise, the key fob itself can also be compromised. If any wireless device with access to the car’s systems is hacked, control of the vehicle can be stolen.
If the vehicle is high value and in especially high demand, there is much more motivation for the bad actors to steal them. Using Bluetooth-enabled wireless repeaters, and thanks to the long range of wireless technologies and their ability to cast beyond physical walls, the bad actors don’t have to be in physical contact with the car or, for that matter, the phone or the key fob, in order to hack into them.
A number of popular vehicle types have been shown to be vulnerable to being stolen with the aid of Bluetooth repeaters. Thieves have been known to boldly walk right up to the front door of the customer’s phone, hold up a big mesh antenna, and try to electronically connect to the key fob. They ping the fob, and the information is relayed to a partner sitting in their getaway car at the curb. Using a laptop and hacker software, they are able to quickly replicate the fob and port that information over to a phone, which in turn is used to access the vehicle and drive it away.
Why is this successful? In part, one contributing element is human nature. Where do most people drop their car keys when they come home? In a little tray or basket near the front door. The bad actors only need the key fob to be located 10 to 15 feet from the front door, to be in range. The rest is simply the manipulation of digital technology, by standing outside at the front door and silently pinging the fob.
This is but one example, at the consumer level. But it illustrates how variables outside the control of the manufacturer, such as the type of phone their customer uses or even where they drop their keys at night, can make a vehicle type vulnerable to generalizations in the press and on social media that can do real damage to a brand’s reputation, earned or not. Yet the manufacturer is expected to anticipate these weaknesses and mitigate them before the sale, because a safe and secure vehicle is the expected default state when a customer buys the vehicle.
What are some of the ways that a supplier might assess the level of cybersecurity they might potentially need, based on their manufacturer’s or their customer’s requirements? Simply put, suppliers are going to do what they have to for the OEM.
There are two different common models for suppliers:
First, there has to be awareness and acknowledgment of the need within the organization. Then, there must be motivation among key personnel, planning, action, and follow-through.
Specifically, how does an organization know when to initiate cybersecurity steps, what steps to initiate, and what they should spend money on? Typically, by comparing and contrasting parallel incidents and scenarios with other organizations that share similar traits to their own. An organization will gain awareness that they need to implement cybersecurity either through:
For example, if an attack happens to another manufacturer, and the organization realizes that they might share similar vulnerabilities to the manufacturer that was attacked, they may logically conclude that they might in turn be vulnerable. This can be highly motivational.
Or, they have gained enough awareness about their industry and customers to realize that they need to implement cybersecurity, either because of risks, or customer demand.
Regardless of the path that takes them to this conclusion, regardless of whether they have pursued this path proactively or have been swept along by events, they reach the point where cybersecurity has been brought to the forefront of their attention, and they can ignore it no longer. They realize that they have to implement cybersecurity. This is a big step, but what is the next one? How does an organization start from square one?
One of the first steps is that the organization has to gain awareness of what they don’t yet know about their overall cybersecurity posture. This can be a very difficult thing for an organization to accomplish accurately and completely, purely by in-house means.
A person or persons might be tasked by the organization to be in charge of cybersecurity, but then what? Yes, there are standards, but first, the newly minted cybersecurity people need to become aware of what those standards are, and even grasp that they need them.
Without guidance, those standards can be imposing and overwhelming, heavy on defining what and in what order, but light on the boots-on-the-ground practical step-by-step details as to how. If your first step is to dive into a single documented procedure that is over 80 pages long for just that procedure alone, that can be very overwhelming. So, the organization has to become properly trained so that their people aren’t wandering in the wilderness.
Cybersecurity is an achievable realm filled with vetted processes that have been proven to work, but it can also be a confusing jungle for the uninitiated. A new person might go through the standard and be confused by it, and not fully understand what is required to create all the documentation and pass an audit. They may not even know that they need to have an audit. They may not know about the UNECE regulations.
It depends on the maturity of the organization as well. If the organization is not yet mature, for example, if they are a recent start-up, they may not yet have all the documentation and processes in place. They may not yet realize that they need a Cyber Security Management System (CSMS). They have a long way to go. And if an organization has to comply with multiple cybersecurity standards, it can really be at a loss because they are not even able to figure out where to start. Where do they begin?
You need guidance, context, and a logical set of processes to follow. You need a guide. You need the kind of training offered by LHP. The practical application of this knowledge is what teaches you how to turn these standards into real-world solutions.
ISO/SAE 21434:2021 “Road Vehicles — Cybersecurity Engineering” is the standard that addresses the cybersecurity perspective in the engineering of electrical and electronic (E/E) systems within road vehicles. LHP offers ISO 21434 training in two forms:
Often, mature companies are simply trying to catch up, trying to meet the knowledge base requirements listed in ISO/SAE 21434:2021 “Road Vehicles — Cybersecurity Engineering”. There is a section in that standard that indicates that the employees of an organization must possess a certain level of competency. That section is rather vague, and there are a number of ways in which that requirement can be met:
If there is an opportunity to both provide certifications and prove competence, there may be a blended scenario where some of the organization’s people need training, while simultaneously, others are creating processes. In what order do these activities need to happen? Can they be approached simultaneously?
In larger organizations, it is natural for people to be at different levels regarding their familiarity with the cybersecurity realm. For example, if someone was just put into a cybersecurity role, they may not even know the terminology yet. Rather than naming this person to a cybersecurity role and then immediately placing them straight into an intensive 4-day certification course, they (and their organization) may instead be better served by first gaining some experience working with the technology, while also gaining familiarity with the various responsibilities that come with working in cybersecurity. As they start to get familiar with the different terminology, the different requirements, and the different responsibilities, they will have a chance to practice applying them. This in turn will help them to be much better prepared to approach the next level, which would be getting themselves cyber-certified through LHP’s ISO 21434 certification training.
The next level after a person becomes cybersecurity certified, is to cascade that knowledge to the organization. This person is now proven to be more qualified to create cybersecurity processes. By applying their proven knowledge, it can flow to different parts of the organization. This helps standardize the entire organization’s requirements and processes.
To maximize your cybersecurity investment in the most efficient manner, you want that high-quality knowledge and insight to flow downward from your best cyber people to the less-experienced people. LHP can help you select the best cybersecurity training solutions to meet your needs, and then work closely to help guide you step-by-step as you drive forward down the path to a safer world.


LHP will be at the 2018 IoT Solutions World Congress Showcasing Embedded Cybersecurity On a Vehicle Platform

Top 5 Automotive Cybersecurity Questions Every Executive Needs to Know Kelly Stephenson, Solutions Architect for LHP, provides product and...
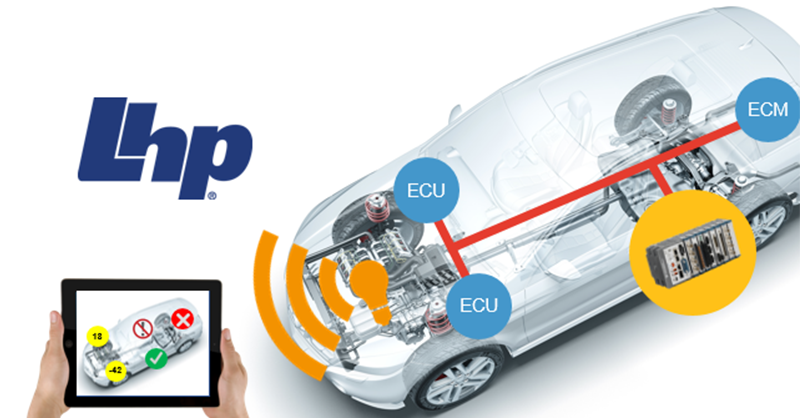
Powered by: LHP Engineering Solutions, AASA Incorporated, National Instruments, and PTC LHP Engineering Solutions, an engineering services provider...